Secrets Management
Securely manage secrets in your Kubernetes cluster with Laralord and HashiCorp Vault
Laralord integrates with HashiCorp Vault to provide secure secrets management for your Kubernetes cluster. Secrets are stored in Vault on the user’s cluster, provisioned via a secure mTLS connection to the Vault server. Users can manage secrets through the Vault UI, seamlessly integrated into the Laralord dashboard, or add secrets directly on the project page. This page details the supported secret types, how to manage them, and how to generate Kubernetes ConfigMaps for your project’s namespace.
Overview
Laralord simplifies secrets management by leveraging HashiCorp Vault to store sensitive data securely on your Kubernetes cluster. Secrets are provisioned using a secure mTLS connection to the user’s Vault server, ensuring encrypted communication. The integrated Vault UI, accessible within the Laralord dashboard, allows users to view, edit, and manage secrets effortlessly.
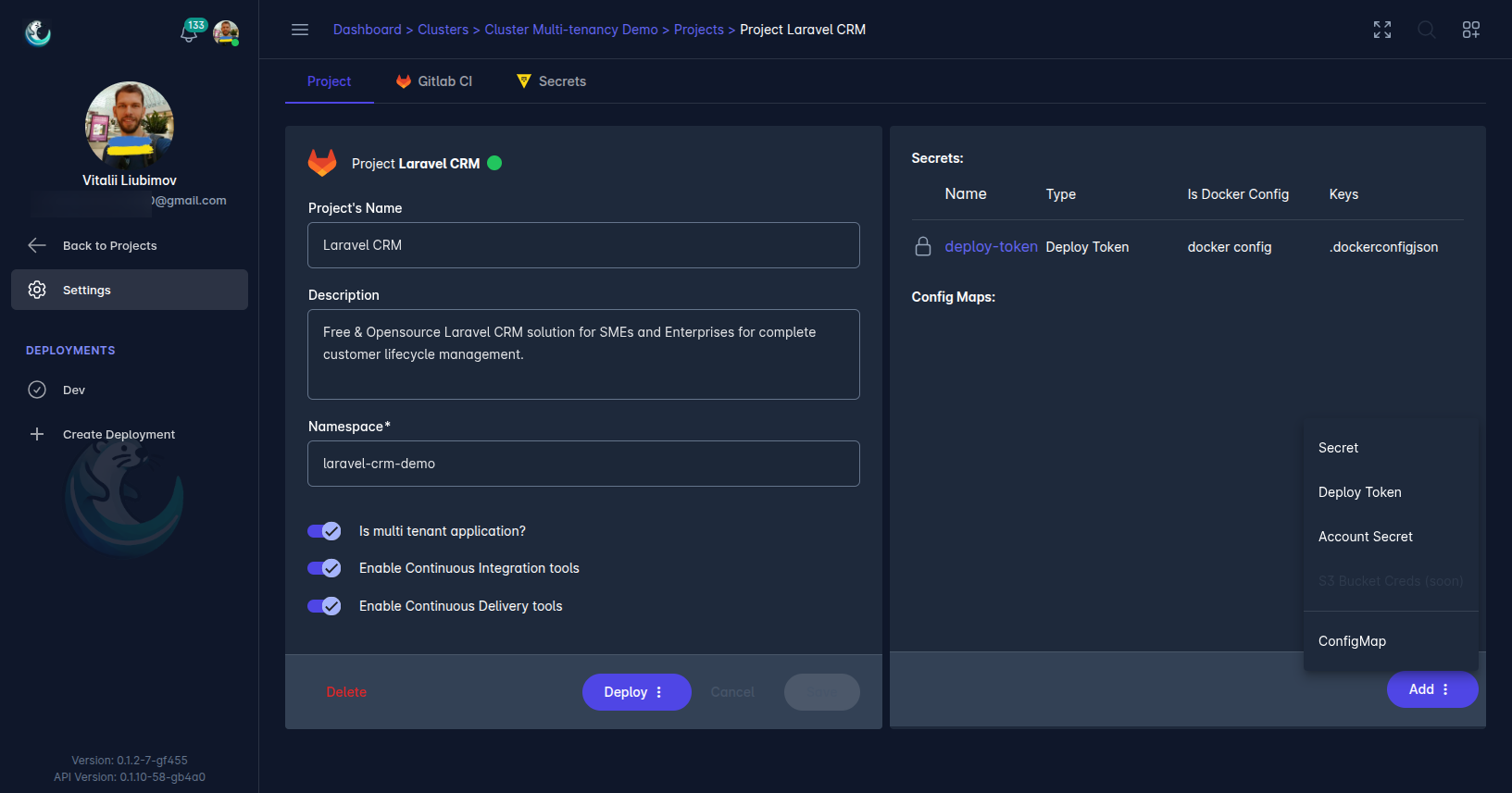
Secrets can also be created directly on the project page, supporting various types tailored to different use cases, such as key-value pairs, Docker registry credentials, and project-scoped deploy tokens. Additionally, Laralord enables the generation of Kubernetes ConfigMaps to inject configuration data into your project’s namespace.
Supported Secret Types
Laralord supports the following secret types, which can be added via the project page in the Laralord dashboard. Each type is designed to address specific needs, such as general configuration, Docker registry access, or project-specific deployments.
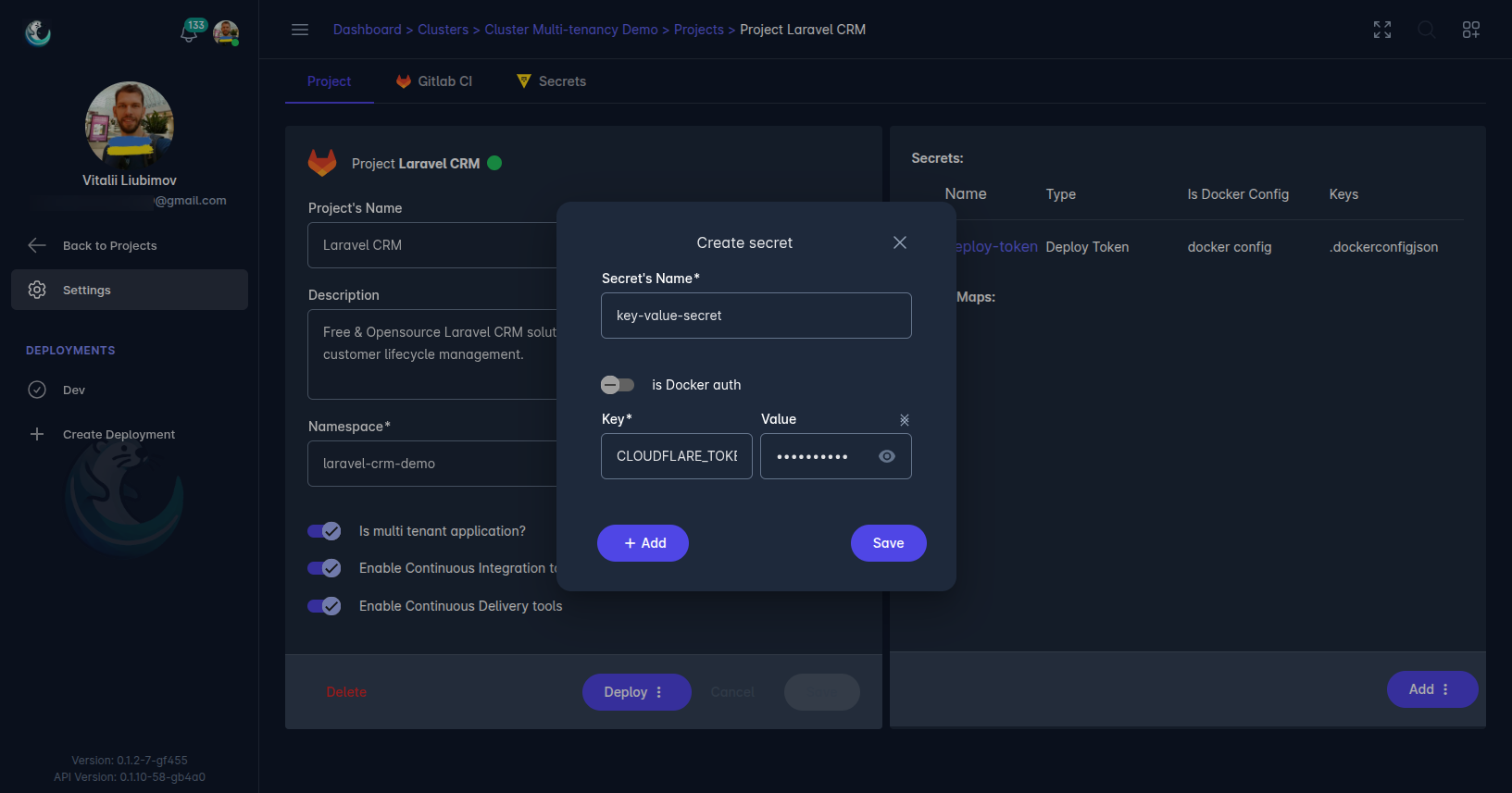
Key-Value Secret
Key-value secrets allow users to store arbitrary key-value pairs in Vault, suitable for storing configuration data, API keys, or other sensitive information. These secrets are versatile and can be used across various applications within your Kubernetes cluster.
Account Secret
Account secrets are used to store credentials, such as a username and token, for accounts that support Docker Registry Authorization. Users can toggle a button to generate a secret in the .dockerconfig format, which is ideal for configuring Kubernetes pods to pull images from private Docker registries (e.g., in the imagePullSecrets field).
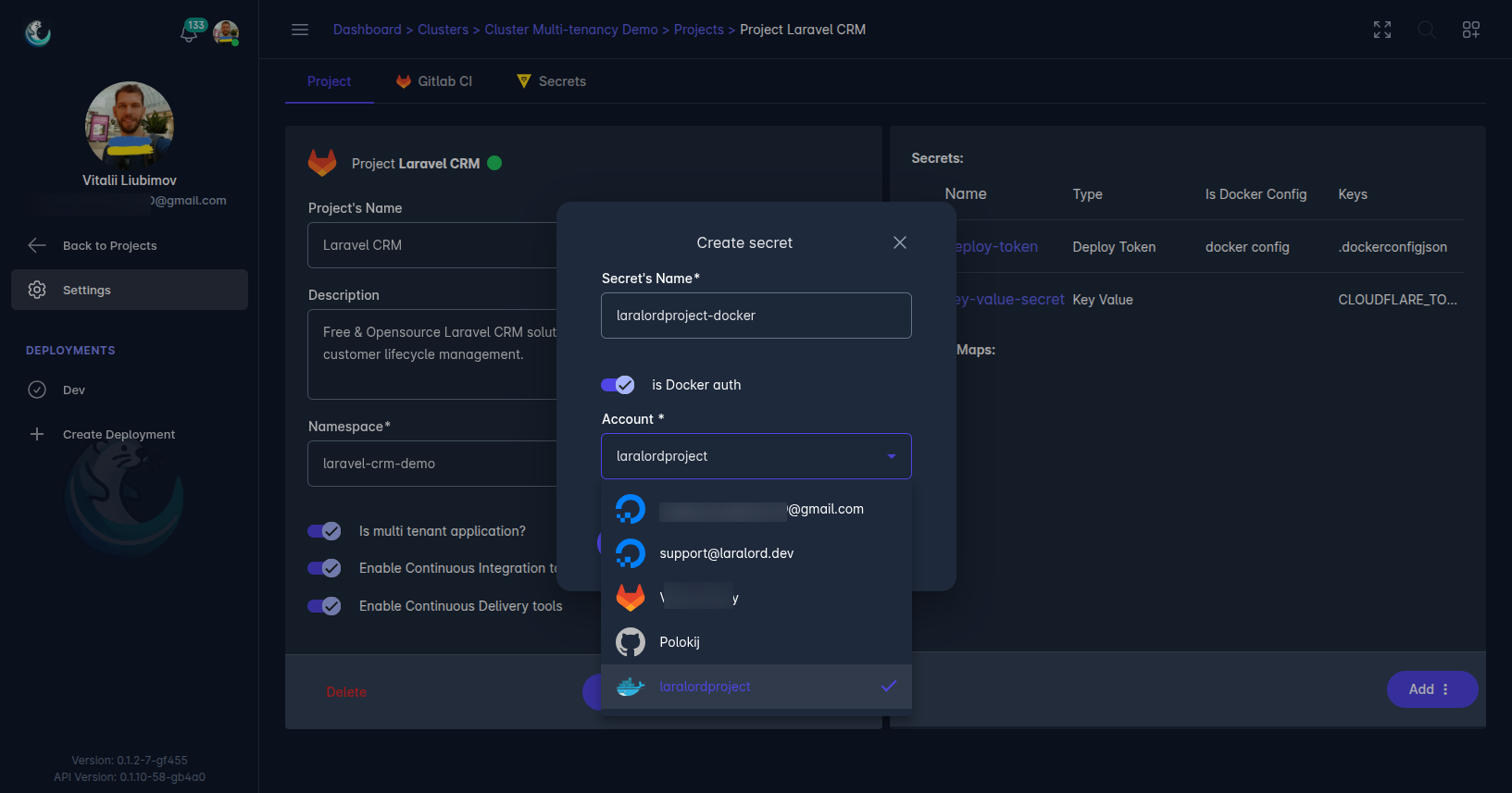
Project Deploy Token
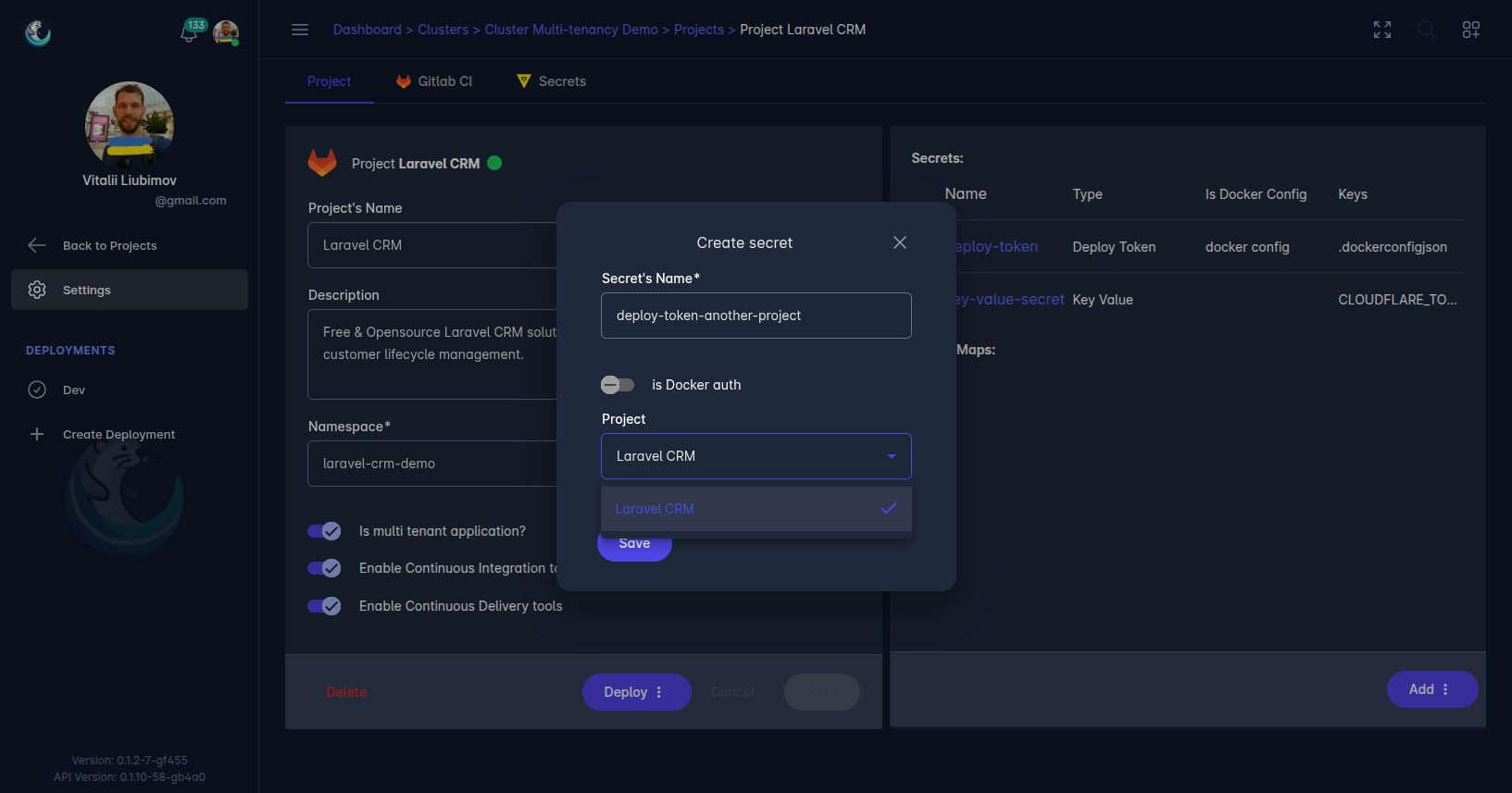
Project deploy tokens are similar to account secrets but are scoped to a specific project, such as a GitHub repository or GitLab project. These tokens have permissions limited to the project’s context, enhancing security. For GitLab projects, users can also generate a .dockerconfig secret to enable access to private Docker registries, similar to account secrets.
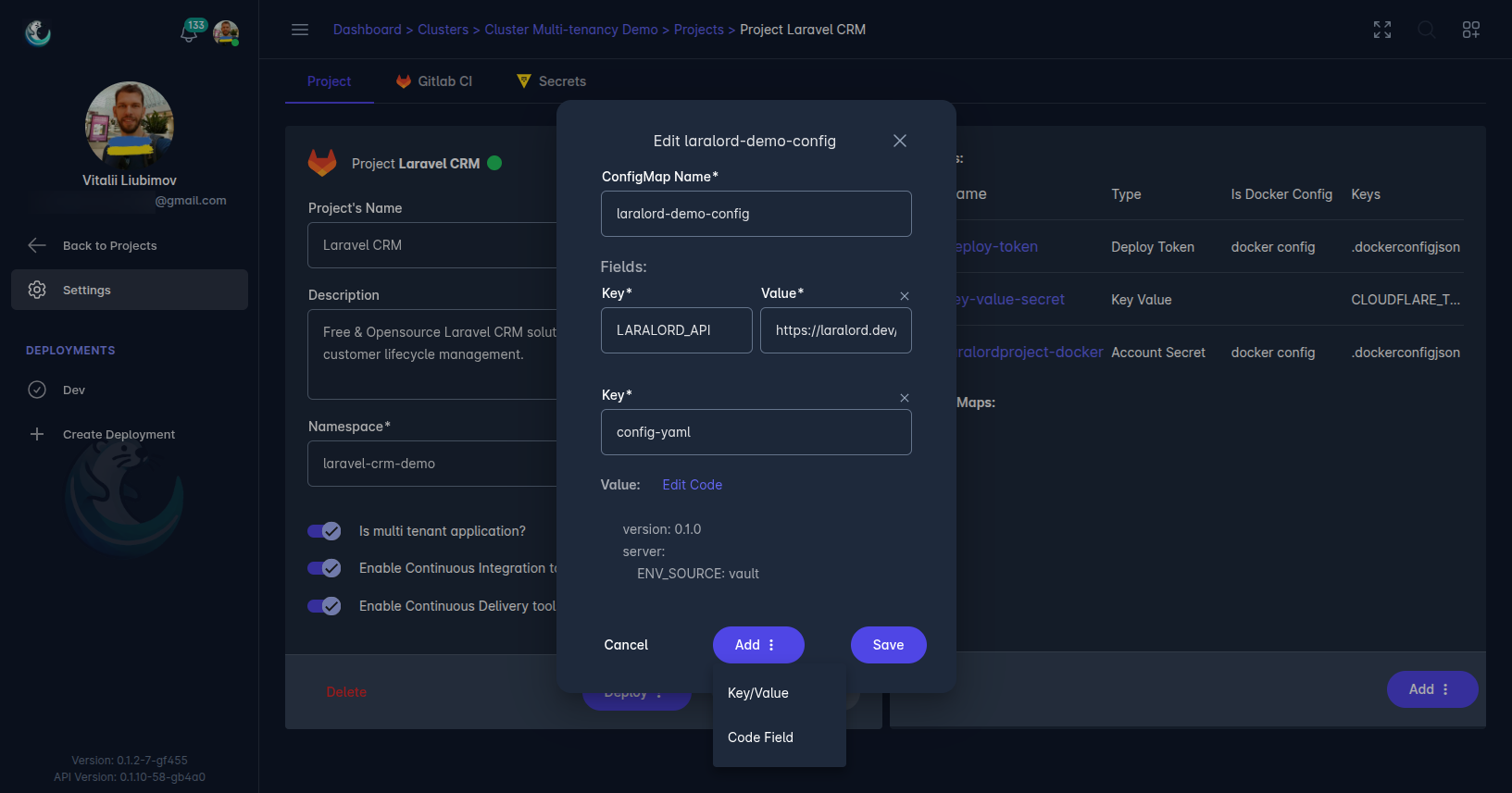
Kubernetes ConfigMaps
Laralord allows users to generate Kubernetes ConfigMaps, which are injected into the project’s namespace to provide configuration data to applications. ConfigMaps support two field types:
- Key/Value: Store simple key-value pairs for configuration settings.
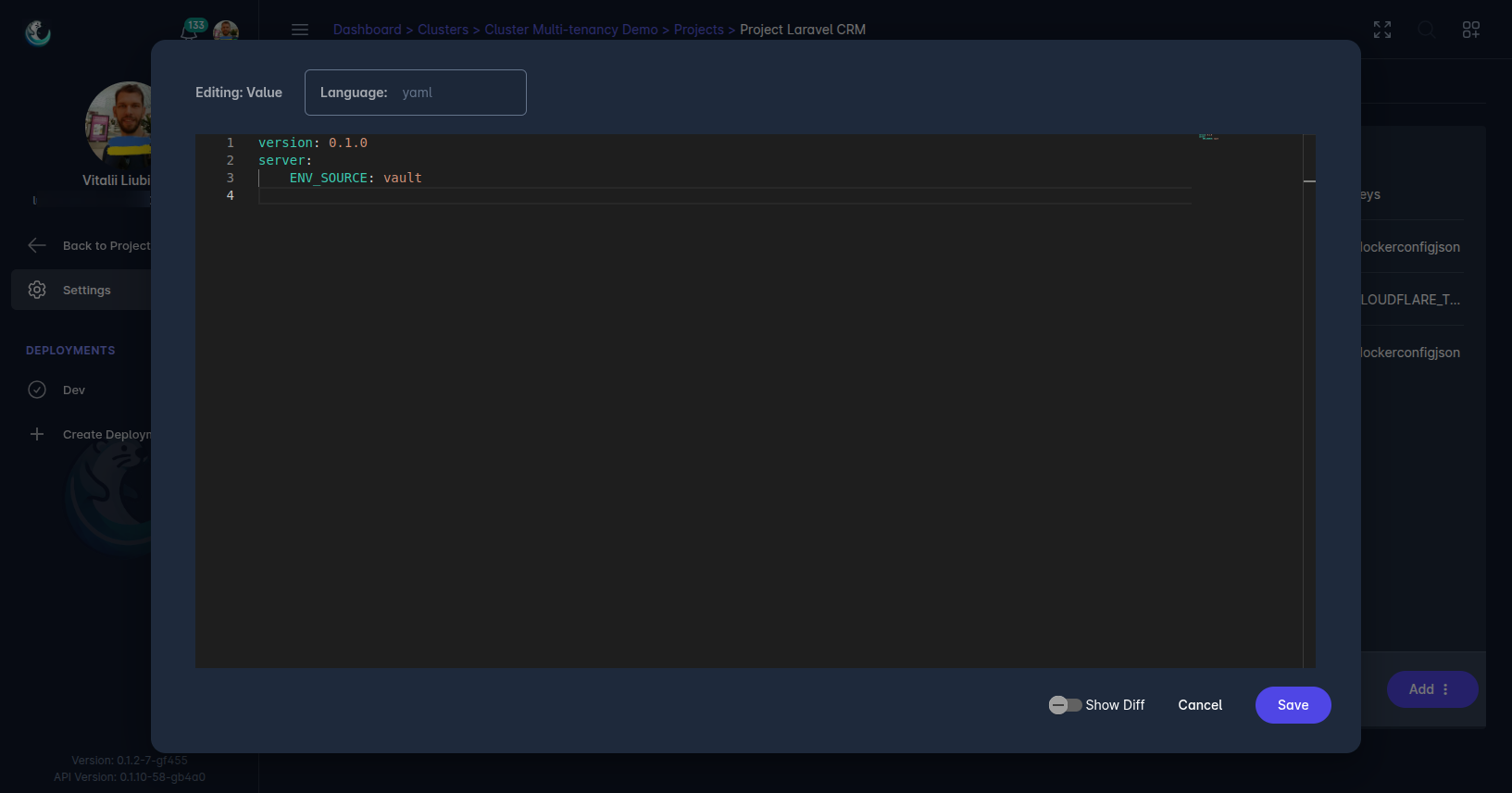
- Key/Code Block: Store larger configuration data, such as scripts or JSON/YAML files, as code blocks.
ConfigMaps are created via the Laralord dashboard and automatically applied to the specified namespace, making it easy to manage application configurations alongside secrets.